Janet called in before 7am and Adam answered on the second ring. “Adam, the site is down. It’s the biggest sales day of the year and our site is down! It was working ten minutes ago and now it won’t load. ” Janet was nervous because this was the busiest shopping day of the year and a big sales day was vital to their success this year.
Adam seemed nonplussed. “Ok, I’ll check right now. I’m sure it’s just increased traffic and I can fix it easily. Don’t worry, boss!” But by the time Janet arrived at the office, Adam had discovered that the problem was far bigger than he’d predicted. “It’s a denial of service. Someone is attacking us, and I don’t know what to do to stop it.”
It was the busiest shopping day of the year and their entire e-commerce operation was dead in the water.

DDoS is serious business and can cripple a network.
Image courtesy of The Joy of Tech
A denial of service attack, or “DoS” attack, occurs when an outside party disrupts a network’s ability to process valid requests. This can mean a barrage of web traffic or manipulative data transfers that confuse and inhibit the network’s capability. DoS attacks are common and can last up to weeks on end. Even scarier, setting off a DoS attack can be inexpensive; attacks that last a week can be put into service for less than $150 on the black market. Every network or website is a potential target and if left unprotected, the administrator is essentially at the mercy of the attacker.
As a point of clarification, a DoS attack takes place when one computer or user initiates the attack, whereas multiple systems are more commonly used. When multiple systems are part of the attack, the result is a distributed denial of service, or “DDoS,” attack or event.
Denial of Service attacks typically take one of four forms:
- Volumetric Attacks: A volumetric attack is the result of an attacker sending more traffic to a website than it can conceivably handle, causing site speeds to slow to a crawl and valid network requests to be denied. In many cases, volumetric attacks actually consume all of the bandwidth connecting a specific site to the internet at large, essentially separating that network from the rest of the connected world. In other words, the site itself is not under attack, but rather the way users access the website is. These attacks can be complicated to prevent since the network transmission system isn’t always under the control of the network administrator.
- Fragmentation Attacks: Fragmentation attacks are the result of hackers or attackers sending broken-up TCP identifiers, or “fragments,” that the network must work to reassemble. Other types of fragmentation attacks include sending messages that tell the victim servers that more information is on the way, although they don’t then deliver that information. The victim network literally waits for information that never arrives (or arrives slowly), which prevents valid use from taking place. The sheer magnitude of fragments or delayed information transmission consumes the network’s available processing power, slowing service to a crawl.
- Connection Attacks: Similar to volumetric attacks, connection attacks work to consume all available connections on a network in an effort to block out valid connections. Websites are not able to support an unlimited number of users and must be built to scale with use. Many websites are able to handle thousands of concurrent users, but very few are able to handle millions of concurrent users. When too many “users” – in this case, spoofed computers and software – try to access the network, then a substantial slow-down occurs.
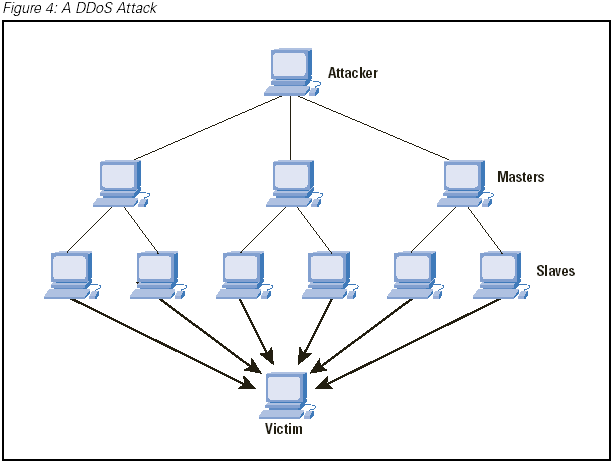
Anatomy of a DDoS attack.
Image courtesy of Cisco - Application Attacks: Application attacks zero in on specific parts of a web application. By overwhelming a specific part of a website, the entire site is crippled and unable to function correctly. For example, a script can be deployed as an attack mechanism that submits a registration form hundreds (or thousands) or times each second to a website. The host web servers would be overwhelmed with processor demand for a small and specific part of the application, which would render the rest of the site useless until the attack ended. This is one of the reasons most web forms require a Captcha or authentication process.
In the coming days we will be examining proper detection techniques and best practices for fighting DDoS attacks. From prevention techniques to what you can do if your network comes under attack, you will learn tools and tips designed to keep your network safe. In the meantime, it’s important to understand that your network and website are vulnerable to DoS attacks and if you’re unprepared like Janet in the example above, your entire organization may be at risk. Click here to learn more about how Mosaic NetworX can help you fight off would-be attackers.




